Date: December 03, 2012
An attack on iPremier’s servers brought to light a lack of planning and
foresight. iPremier lacked a formal
emergency plan, had poor communication with management, and inadequate equipment
with their partner, QData. The
attack itself could have been handled more appropriately or even avoided
entirely. There are certain
decisions that could have been handled differently to avoid the outcome that
transpired.
Founded in 1994 by two college students, iPremier was one of the leading
online retail stores for luxurious and vintage goods.
They were also one of the few survivors surviving the Dot-com crash.
It is important to understand the company’s background and culture in
order to understand how and why the attack on iPremier occurred in the first
place.
The management and culture consisted of a mix of young talented employees
and a few experienced managers.
This allowed management to have a balanced approach to growth and profitability
but still focus on growth. The
management’s compensation was based on performance, creating an intense
atmosphere focused on “doing whatever it takes” to finish projects on time and
before competitors. Managers with
low performance numbers did not last long.
One of the only aspects not directly controlled by iPremier was that of
its IT. The management of its
technical architecture was outsourced to QData, an early partner of iPremier’s.
QData provided floor space, power, connectivity, and physical software
security. iPremier considered
switching partners for their IT infrastructure but had several reasons against
such a decision which they considered disadvantageous.
The first reason was the cost of floor space where it was 203 times
cheaper per square foot than any of the closest competitors.
A higher cost of operating their servers would have resulted in a hit on
profitability, something iPremier was hesitant to accept.
The second reason was the downtime that would result with such a move.
The last reason was a personal commitment the founders of iPremier had
towards QData. Since iPremier’s
beginning, QData was a partner and switching to a competitor felt like a
betrayal. The choice of not moving
to a superior competitor would later cost iPremier a great deal more than money
when they came under a cyber-attack.
Pillars
of IT in the Case
First, the goals that should be established are: minimize the likelihood of an
attack, develop ways to quickly recover from an attack with little interruption
and apply high standards for backing up systems, training, and security which
will includes patch application to lessen likelihood of a recurrence.
It will be helpful to set up a policy
that constantly assesses all possible viruses/threats as well as keeping a
current idea with patch application to deflect off future attacks.
Better protection for their systems can
be achievable and get services of external consultants to periodically assess
their systems for weaknesses/vulnerabilities and to determine the best
solutions/courses of action. iPremier
should also have a contingency plan and possibly a call center for technical
support. iPremier needs to move to
modern hosting facility, modernize its computing infrastructure to include a
more sophisticated firewall, more appropriate security/privacy measures,
cryptograph for sensitive data, message integrity algorithms to determine if
files have been modified/corrupted, enabling logging and determine the level of
logging. Also, iPremier should purchase
disk space to enable higher levels of logging and update its virus signature
files and security patches. Lastly, test
to ensure that they would be able to restore from those backups.
Qdata needed to ensure that they can
guard against attacks, and its applications and services, particularly for
essential/critical systems available (Glossary, 2011).
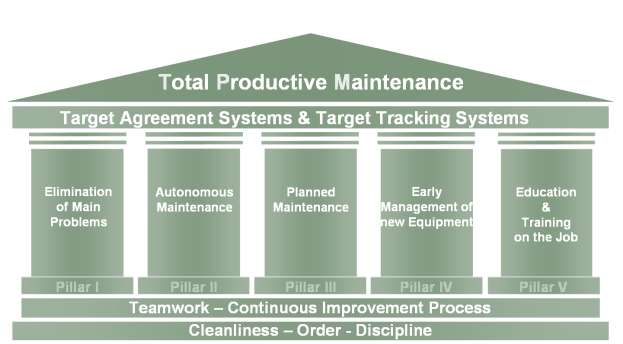
iPremier could support its operation in the Total Productive Maintenance five
pillars:
·
Elimination of main problem: Outsource its core business
·
Autonomous maintenance: Take responsibility in its own hands
·
Planned
Maintenance: Create policies and contingency plans
·
Early
Management of new equipment: Invest smartly in security of its infrastructure
·
Education and training on the job: Prepare the personnel to deal with common IT
related
problems
that it can face.

The attack on iPremier’s servers began at 4:31 in the morning and lasted
a little over an hour. During that
time, the management at iPremier committed several mistakes including one key
misstep during the pivotal point.
The largest mistake and pivotal point occurred at 4:39am when Joanne Ripley, the
technical operations leader, decided to keep the servers online instead of
pulling the plug. This decision
allowed the attackers to later penetrate the firewall and compromise the servers
holding credit card data. There
were both situational and system failures during this timeframe.
The system had a near nonexistent firewall and iPremier had no access
remotely which led to very limited information about the attack.
Additionally, a poor contingency and communications plan resulted in the
wrong actions and a lack of communication between team members.
If iPremier had taken different steps such as shutting down the servers
or communicated more effectively, the pivotal point may have resulted in a
brighter future than they later experienced.
Before the attack, the company sells luxury, rare, and vintage goods over the
Internet. The goods normally
priced for under $200. Customers buy
stuff with their credit cards. The
company also offered very flexible return policies.
They became one of the only few success stories of web-based commerce.
In the beginning, the company started
with young people and a group of experienced managers (CIO, Bob Turley, CEO,
Jack Samuelson, and IT manager, Joanne). The
headquarters was located near Qdata and had contracted with Qdata.
Qdata provided most of their computer
equipment and connectivity to the Internet;
iPremier did not have the ability to access to their data center at
Qdata immediately, and an emergency procedure was not being readily available.
The attack put the company into trouble
with the customers and the investors. They
lost their credibility and the business revenue dropped dramatically.
After the attack, the company should still sell luxury, rare, and
vintage goods. They can sell stuff that
priced for over $200. The new system
could accept credit card payment and some popular secure payment like PayPal or
Google Checkout. Flexible return
policies are necessary for any web-based commerce.
They try to keep being one of the only
success stories of web-based commerce. After
updating the emergency procedure, the company offers better training in
employees for emergencies. Moving the
system to a reputable hosting provider with a world-class infrastructure and
support rather than Qdata and choose redundancy planning and testing.
A risk management program should
identify, analyze, evaluate, treat, monitor and communicate the impact of risk
on IT processes. The IT risk framework
also has three major domains- risk governance, risk evaluation and risk
response. The risk response from this
attack should be documented and reviewed by IT steering committee as guidelines
to support future potential attack. The
goal is to regain credibility and assure to the customers that company is
working in the best interest of the customers
Tactical Steps
The first step in determining if outsourcing your IT infrastructure is right for
your business is to conduct a thorough assessment of your existing
infrastructure and applications.
Then with all stages of this five-step process, this procedure is most
effective when conducted with the help of a qualified service provider.
It is crucial that they have proven expertise in identifying what IT
components and functions. If after
consideration of the above steps you are committed to outsourcing by selecting
an experienced vendor able to manage your IT infrastructure effectively, you
will be able to focus clearly on your business whilst the service provider
manages and monitors your virtualized infrastructure to ensure system
availability and efficiency. A cloud
provider that has networking expertise as well will help to ensure the network
element of the cloud service is optimized you must choose your provider
carefully.
FireWall-1 provides transparent, selective encryption for a wide range of
services, allowing organizations to make full use of the Internet for all
business and connectivity needs. Multiple
encryption schemes, key management and an internal Certificate Authority are
fully integrated with other FireWall-1 features.
FireWall-1's intuitive graphical interface makes it simple to define and
manage encryption in an enterprise security policy.
Firewall gateways can encrypt data
communications traveling over the Internet between disparate networks, thereby
creating a secure or Virtual Private Network. FireWall-1
implements encryption for corporate internetworks without the need to install
and configure encryption software on each host in each network involved
(Articles, 2011)
.
Then, a FireWall-1 gateway performs encryption on behalf of its encryption
domain the local area network (LAN) or group of networks that it protects.
Packets traveling over the public
segment of the connection are encrypted, while on the internal network - behind
the gateway - packets are not encrypted.
Being
an industry leader today is in no way a security blanket to confirm tomorrow's
success. In order to maintain
competitive advantage and emerge as an industry leader tomorrow, established old
school companies must be ready to take on the challenge of some difficult and
painful changes. Not only in leveraging
IT to its limit but also to change the way employees and administration think
and work to a whole new level (Articles, 2011).
The iPremier technology was not harmed but the earnings of the company plummeted
due to a denial of service attack and a SYN flood attack.
“Denial of service is a form of attack on the availability of some
service. In the context of computer
and communication security, the focus is generally on network services that are
attacked over their network connection” (Stallings, W., 2008).
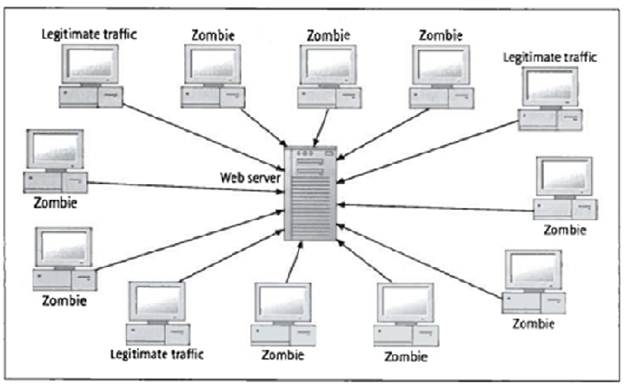
“A distributed denial of service, or DDoS, attack is an attack that is
designed to disable a network by flooding it with useless traffic.
To launch a DDoS, a hacker might first compromise multiple personal
computers by installing Trojan horse programs that allow the hacker to control
these computers remotely. Then the
hacker would use the compromised or “zombie” computers to send continual stream
of traffic to a Web server. This
stream not only disrupts the real traffic at the Web site, but it ultimately
crashes the server, which tries to respond to the excess traffic” (H. A. Napier,
2006). Figure 1 shows a DDoS attack
below.
Figure 1 – DDoS Attack
“An
online bookseller like Amazon.com can come from nowhere, go public, and make its
founder worth over $300 million as it becomes one of the world’s largest book
distributors within a couple of years.
Two graduate students can brainstorm an idea, develop a search engine
that acts like the Yellow Pages for the Web, get venture capital funding
and go public as Yahoo, each worth hundreds of millions of dollars before their
30th birthdays” (Young,
J.,1999).
Finally, iPremier suffered from a SYN flood attack promoted by a denial of
service action. When iPremier was
experiencing a SYN flood, their customers could not access the Web site to
purchase anything, nor could administrators log in from a telnet connection.
“The basic premise behind this option is to launch decoy scans at the
same time a real scan is launched” (McClure,
S., 2009). This is achieved
by spoofing the source address of iPremier’s servers using the real port scan.
Since the iPremier address was alive, the scans implemented a SYN-flood
attack using the server email system and caused a denial of service attack that
ultimately closed down the iPremier site.
Non-technology Factors
Non technology factors would primarily concern for human resources to do a
better background check for the person they hire.
A great guideline for the employee is
they should have been in the field of IT for at least 5 to 10 years for him/her
to be hired. The required skills for an
employee should pertain to more knowledge of the type of work that is required
from him/her at iPremier and be a team leader with more experience in IT than
their leading competitors.
Training should include but not limited to keep all information and server on
site. Keep all credit card numbers
and passwords encrypted within a table. One
table might contain the half of the digits of the credit cards and another one
the other half; a third table may contain the rest of the data (Encryption).
Now, you need a table that holds all the relations between them. That table
should be encrypted using MD5 or something alike. It would be good practice to
not forget to change the password/encryption string.
Don't save the data on your webserver,
better forward these as encrypted info to your back up server.
Each time a client wants to buy, just assure that he is who he claims to be by
using somewhat authentication and then only forward references to his user info
stored on your intranet server, where you need some tool to generate the billing
process, cause you can bill credit cards also in real world (Encryption).
There are numerous lessons that can be taken away from this case study,
many of which could have easily been avoided if proper action had occurred prior
to the attack. The first lesson is
the consideration of all business partners.
iPremier relied too heavily on QData resulting in numerous difficulties
during the attack. If iPremier had
seriously reconsidered their partnership with QData, the attack might never have
taken place. Today, the economic
downturn has caused many businesses to experience increased threats against
their networks. Businesses must
innovate and adopt the latest technologies to stay competitive but improper
security of these new technologies can lead to data theft and corruption (Emel,
D., 2010). However it is nearly
impossible to guarantee protection from an outside attack making a risk plan
during crises extremely important.
Without a risk plan, a company’s management will proceed “reactively” rather
than in a controlled manor. This
can easily cause additional missteps and cost more than the initial effort a
risk plan requires (Heagney, J., 2012).
A course of action during certain planned risk scenarios can lead to
faster and more appropriate decisions during an attack, especially during a key
pivotal point. iPremier was
hesitant to pull the plug to the servers during the initial moments of the
attack and instead left them on.
There should have been a clear plan as to how the team would proceed in the case
of such an attack. Part of their
problem was the fact that there was no communications plan outlined causing a
breakdown in the information flow.
“Excellent crisis management cannot exist without excellent communication”
(Marra, F., 1998). A communications
plan during a crisis can lead to faster results; if iPremier had a plan
outlining employees to contact during a crisis, the crises may have ended
different or possibly avoided entirely.
According to the industry standards, when a business is assembling their
products or services they need to user verifiable data that has been gathered
from recognized sources such as government agencies and industry trade
associations. Therefore, iPremier should
have gathered information from the United States government patent agency.
Each of your major competitors should be identified by name; according to
the industry standards (Wagner, 2006). Then,
iPremier teamed up with Qdata to set up a colocation to increase security and
protect the iPremier servers from being attacked by an adversary.
Qdata
is still in business today and teamed up with Viascan Group to create Canada’s
leader in barcoding and wireless networking solutions (Qdata, 2012).
However, the same cannot be said about iPremier.
Next, iPremier was attacked on January 12, 2001.
Now, iPremier should have taken further precautions in researching how to
protect their revenue from falling.
There
have been eight patents designed to stop SYN attack flooding for email servers
developed and implemented before iPremier was attacked.
“A flexible, event driven and conditional rule based mail messaging
system which can be transparently implemented for use in electronic mail
applications. A rule mechanism is
implemented having a "When-If-Then" event-driven, conditional, action-invoking
paradigm or "triplet" which permits definition of a repertoire of events
considered to be significant events upon which to trigger actions in the
electronic mail messaging system.
Each
particular event may be associated with a specific mail message and/or rules to
promote efficient mapping of messages, events and rules so that only rules
associated with a specific event are invoked upon occurrence of the event.
Only relevant rules, i.e. those
associated with a satisfied event, need be further processed.
A graphical user interface to a
structured rule editor facilitates synthesis of rules by a user via a
substantially transparent rule engine” this was in February of 1994(US patent
5283856).
In
December 1994, a method and system for sorting and prioritizing electronic mail
messages was patented and could have kept iPremier’s email from being flooded
(US patent 5377354). In April of
1997 techniques for reducing the amount of junk e-mail received by a user of an
e-mail system was patented (US Patent 5619648).
In October of 1998, an apparatus, methods, and computer program products
are disclosed to simplify a computer user's handling of electronic mail
messages. The invention provides the
computer user with a mechanism for ignoring a particular ongoing e-mail
discussion until that ongoing discussion terminates; this could have terminated
the ‘ha’ email messages (US Patent 5826022).
On
December 7, 1999 “A system for eliminating unsolicited electronic mail generates
and stores a user inclusion list including identification data for identifying
e-mail desired by the user. Data from
one or more fields of incoming electronic mail messages are compared with the
identification data stored in the user inclusion list.
If the electronic mail message data
matches corresponding identification data from the user inclusion list, the
e-mail message is marked with a first display code, such as "OK."
If no match is detected, the system
performs at least one heuristic process to determine whether the electronic mail
message may be of interest to the user. If
the message satisfies one or more criteria as determined by the heuristic
process and is therefore of potential interest to the user, the message is
marked with a second display code, such as "NEW".
If the e-mail message does not satisfy
any of the heuristic criteria, the e-mail message may be marked with a third
display code, such as "JUNK." The
processed e-mail messages are displayed to the user in a display mode
corresponding to the display codes respectively assigned to the messages” (US
Patent 5999932). Again in 2000 a
patent was filed that included a method is provided for preventing the delivery
of unwanted electronic mail messages to a destination client (US Patent
6112227).
In
conclusion, I would have recommended any of these ideas for iPremier and the IT
manager should have looked further into these patents and would have read the
basics of how to use them and implement the steps into their computer
architecture that could have led to a number one online selling site just like
Amazon.
Applegate, L. M., Austin, R. D., McFarlan, F. W., & Applegate, L. M. (2003). The
iPremier Company: Denial of Service Attack. In Corporate information strategy
and management: Text and cases (pp. 491-499). Boston: McGraw-Hill Irwin.
Articles. (2011, November 14). Five
Steps to Outsourcing Your Business IT Functions to the Cloud âº.
Retrieved November 30, 2012, from
http://www.thedatachain.com/articles/2011/11/five_steps_to_outsourcing_your_business_it_functions_to_the_cloud
Encryption. (1999). Encryption. Retrieved from
http://www.dm-int.com/Encryption.htm
Emel,
D. (2010). The Evolving Role of Security Structures. Retrieved December 3, 2012,
from
http://www.sans.org/reading_room/whitepapers/leadership/evolving-role-security-structures_33264
Flanagan, R. (2012, November 9). MIS 5202 IT Governance Fall 2012. MIS 5202 IT
Governance Fall 2012. Retrieved from
https://community.mis.temple.edu/mis5202flanaganfall2012/2012/11/09/ipremier-denial-of-service-attack-case/
Glossary. (2011). - Unified Process for EDUcation. Retrieved November 26, 2012,
from http://www.upedu.org/process/glossary.html
Heagney, J. (2012). Fundamentals of Project Management. (4th ed., pp. 55-67).
New York: Amacom
IT Model Curriculum. (2012). ACMSIGITE L Special Interest Group for Information
Technology IT Model Curriculum Comments. Retrieved November 26, 2012, from
http://www.sigite.org/it-model-curriculum
Lynda M Applegate, R. D. (2008). Corporate Information Strategy and Management:
Text and Cases. McGraw-Hill/Irwin.
Marra,
F. (1998). The important of communication in excellent crisis management.
Retrieved December 3, 2012, from
http://www.em.gov.au/Documents/The_importance_of_communication_in_excellent_crisis_management.pdf
McClure, S., Scambray, J., & Kurtz, G. (2009). Scanning. In Hacking exposed 6:
Network security secrets & solutions (6th ed., pp. 649-653). New York:
McGraw-Hill.
Piyush, R., Wilson, W. J., Haldar, P. D., Chandler, J., & Debashis, W.
(2012). U.S. Patent No. 8301712. Washington, DC: U.S. Patent and Trademark
Office.
Qdata merges with the viascan group to create canada's leader in barcoding,
rfid, and wireless networking solutions. (2012, February 28). Canada Newswire.
Retrieved November 08, 2012, from
http://ehis.ebscohost.com/eds/detail?sid=af851f54-cc0f-4f83-9361-132073b99879%40sessionmgr111&vid=3&hid=103&bdata=JnNpdGU9ZWRzLWxpdmUmc2NvcGU9c2l0ZQ%3d%3d#db=bwh&AN=201202281452CANADANWCANADAPR.C8155
Robert D. Austin, L. L. (2007, 07 26). iPremier Co. (A): Denial of Service
Attack. Harvard Business Publishing.
Young, J. (1999). Webs Networks & the Internet. In Forbes greatest technology
stories: Inspiring tales of the entrepreneurs and inventors who revolutionized
modern business. (pp. 342-343). New York: Wiley.
Rivers, O., Wagner, S., & Napier, J. B.
(2006). Securing your e-business. In H. A. Napier (Author), Creating a winning
E-business (2nd ed., pp. 379-380). Boston, MA: Thomson Course Technology.