
Guide to Patent
Software
Major: Information Technology
Date: December 06, 2012
The way to get ahead in the technology field is to
patent your ideas and keep your intellectual property safe.
This way, a manager can research the Unites States Patent office for
tools to protect their business by not having to reinvent the wheel.
The process of keeping your ideas and inventions safe will be revealed by
informing the reader how to search the US Patent office database, keep official
documentation of the patent, and how to be successful in the process while using
the industry standards. The case
study with the iPremier Company suffered a denial of service attack from a
SYN-flood and a denial of service attack.
The company could have avoided the loss of their revenue if they would
have prepared for high risks by researching the patents and using the step by
step guides for industry standards.
The forms for creating a guide to protect and profit from patents will be
discussed. The one way to file for
a patent was researched to add on to the Information Technology Management
classes’ team project to inform the reader how to file and maintain inventions
to better the economy.
There is some time and money invested to devolving a
patent. The inventor will need
around $200 dollars for patent office fees and payments; a patent application,
sole inventor, petition, power of attorney and oath; a document that states the
patent application, joint inventors, petition, power of attorney and oath; a
sample agreement of contract between the inventor and manufacturer; company
requirements for consideration of outside inventions or a sample statement
policy; assignment of patent and application (Kessler, 1965).
The reader may conduct their own search
by going to their local library and searching for all books within the card
catalog that has the keyword ‘patent’.
The researcher should then continue onto the surrounding counties and
libraries for further searching. To
keep the search contained, move onto the US patent office database online at
patft.uspto.gov and type in what keywords are within the invention you are
thinking of. The results will prove
if someone has thought of your idea before; if no results are found then perhaps
call the patent and trademark office at (703) 308-5278 for a roster of patent
attorneys to help with your search.
Finally, when there are no results of your search continue with the application
process to patent your invention.
The
author used this approach to find out the industry standards and possible
patents to stop a denial of service attack for a case study on the iPremier
company attack in 2001.
The iPremier technology was not harmed but the earnings of the company plummeted
due to a denial of service attack.
“Denial of service is a form of attack on the availability of some service.
In the context of computer and communication security, the focus is
generally on network services that are attacked over their network connection”
(Stallings, W., 2008). “A
distributed denial of service, or DDoS, attack is an attack that is designed to
disable a network by flooding it with useless traffic.
To launch a DDoS, a hacker might first compromise multiple personal
computers by installing Trojan horse programs that allow the hacker to control
these computers remotely. Then the
hacker would use the compromised or “zombie” computers to send continual stream
of traffic to a Web server. This
stream not only disrupts the real traffic at the Web site, but it ultimately
crashes the server, which tries to respond to the excess traffic” (H. A. Napier,
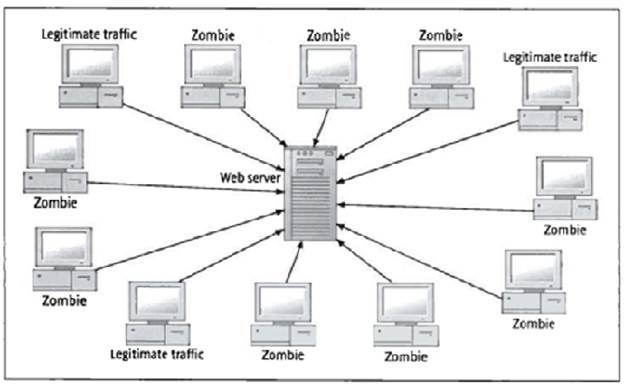
2006). Figure 5 shows a DDoS attack.
“An
online bookseller like Amazon.com can come from nowhere, go public, and make its
founder worth over $300 million as it becomes one of the world’s largest book
distributors within a couple of years.
Two graduate students can brainstorm an idea, develop a search engine
that acts like the Yellow Pages for the Web, get venture capital funding
and go public as Yahoo!, each worth hundreds of millions of dollars before their
30th birthdays” (Young,
J.,1999).
Finally, iPremier suffered from a SYN flood attack promoted by a denial of
service action. When iPremier was
experiencing a SYN flood, their customers could not access the Web site to
purchase anything, nor could administrators log in from a telnet connection.
“The basic premise behind this option is to launch decoy scans at the
same time a real scan is launched” (McClure,
S., 2009). This is achieved
by spoofing the source address of iPremier’s servers using the real port scan.
Since the iPremier address was alive, the scans implemented a SYN-flood
attack using the server email system and caused a denial of service attack that
ultimately closed down the iPremier site.
One can easily tell the difference between the way a
patent application use to be in Figure 4 and the layout of todays in Figure 6.
This form is first needed to start a filing process for a patent.
If you are an inventor, business advisor, manager, CEO, educator or a
developer then it will be behoove you to learn the process of filing a patent.
To apply for a patent the proper application must be sent
to the Commissioner of Patents like the one you can see in Figure 6.
The application consists of an application fee, a petition, a
specification and claims describing and defining the invention, an oath, and
drawing if the invention can be illustrated (Kessler, 1965).
In order to prepare yourself for the patent process,
keeping a journal can help you stay on track.
An inventor should keep a potential user survey that can describe the
pros and cons of your invention. A
proprietary materials agreement should be recorded for any materials loaned to
you to complete the invention.
Also, come up with a positive and negative table to evaluate your invention.
If you have been selling your invention for longer than the period of one
year without a patent, the invention is non-patentable.
The fees to file a patent on your own without a patent
attorney or agents will consist of: Disclosure document fee for $10; Provisional
Patent filing fee $150; Printed Copy of Patent fee $3; and Copy of Patent with
Color Drawings fee $25 (Pressman, 2000).
You can file your own patent for around $200.
The patent will stay in the database and protected for as
long as the maintenance fees are paid up to date.
A patent maintenance fee for the first phase is payable at three to three
and a half years after filing for $850.
The second phase of fees totaling $1,950 is due seven to seven and a half
years after issuance. The third
phase is payable 11 to 12 years after the issue of a patent for $2,990
(Pressman, 2000).
The fees will continue to increase as long as the patent
is kept of file within the patent office database.
Once the inventor can sell the idea, the maintenance fees are no longer
of interest to the original inventor.
Now, review the following to understand how to conduct a
patent search online. The figures
listed below will show you what today’s patent office website looks like and
where you should be during the navigation.
First, open up any web browser on the computer.
Then, type this website into the search box at the top of the web
browser: http://www.patft.uspto.gov/ .
The introduction page to the United States Patent and Trademark Office
(USPTO) will be on the monitor like the picture below.

Now, there are more than a few ways to conduct a search on here.
The way to go if you’re doing research on current patents is to click on
the link “Quick Search” on the left side of the screen under the Patents column.
You will now come to a page like this one below:
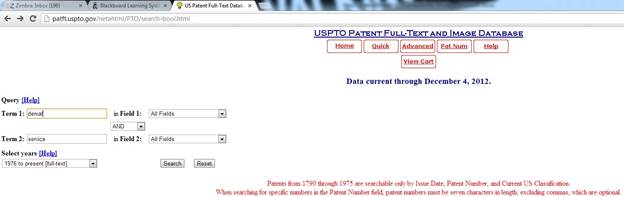
Figure 2 – Boolean Search
Next, this search option is only completed when the user selects two
terms with a selected Boolean. For
this topic it was best to input ‘denial’ in the Term 1 box.
Then, type ‘service’ in the Term 2 box and keep the AND as is in the drop
down box and click the search button.
Then, the database will direct the user to all patents that contains the
words denial and service. This
search was selected for the denial of service attack on the iPremier company
case study. The results from the
search are pictured below:
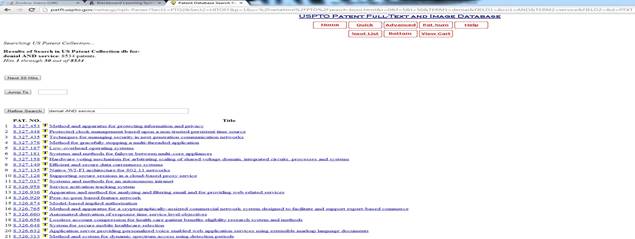
Figure 3 – Denial of Service
Patent Results
According to the industry standards, when a business is assembling their
products or services they need to user verifiable data that has been gathered
from recognized sources such as government agencies and industry trade
associations. Therefore, iPremier
should have gathered information from the United States government patent
agency. Each of your major
competitors should be identified by name; according to the industry standards
(Wagner, 2006). Then, iPremier
teamed up with Qdata to set up a colocation to increase security and protect the
iPremier servers from being attacked by an adversary.
Qdata
is still in business today and teamed up with Viascan Group to create Canada’s
leader in barcoding and wireless networking solutions (Qdata, 2012).
However, the same cannot be said about iPremier.
Next, iPremier was attacked on January 12, 2001.
iPremier should have taken further precautions in researching how to
protect their revenue from falling.
There
have been eight patents designed to stop SYN attack flooding for email servers
developed and implemented before iPremier was attacked.
“A flexible, event driven and conditional rule based mail messaging
system which can be transparently implemented for use in electronic mail
applications. A rule mechanism is implemented having a “When-If-Then”
event-driven, conditional, action-invoking paradigm or “triplet” which permits
definition of a repertoire of events considered to be significant events upon
which to trigger actions in the electronic mail messaging system.
Each
particular event may be associated with a specific mail message and/or rules to
promote efficient mapping of messages, events and rules so that only rules
associated with a specific event are invoked upon occurrence of the event.
A graphical user interface to a
structured rule editor facilitates synthesis of rules by a user via a
substantially transparent rule engine” this was in February of 1994(US patent
5283856).
In
December 1994 a method and system for sorting and prioritizing electronic mail
messages was patented and could have kept iPremier’s email from being flooded
(US patent 5377354). In April of
1997 techniques for reducing the amount of junk e-mail received by a user of an
e-mail system was patented (US Patent 5619648).
In October of 1998 an apparatus, methods, and computer program products
are disclosed to simplify a computer user’s handling of electronic mail
messages. The invention provides the computer user with a mechanism for ignoring
a particular ongoing e-mail discussion until that ongoing discussion terminates
(US Patent 5826022). This could
have terminated the ‘ha’ email messages.
On
December 7, 1999 “A system for eliminating unsolicited electronic mail generates
and stores a user inclusion list including identification data for identifying
e-mail desired by the user. Data from one or more fields of incoming electronic
mail messages are compared with the identification data stored in the user
inclusion list. If the electronic mail message data matches corresponding
identification data from the user inclusion list, the e-mail message is marked
with a first display code, such as “OK.” If no match is detected, the system
performs at least one heuristic process to determine whether the electronic mail
message may be of interest to the user. If the message satisfies one or more
criteria as determined by the heuristic process and is therefore of potential
interest to the user, the message is marked with a second display code, such as
“NEW.” If the e-mail message does not satisfy any of the heuristic criteria, the
e-mail message may be marked with a third display code, such as “JUNK.” The
processed e-mail messages are displayed to the user in a display mode
corresponding to the display codes respectively assigned to the messages” (US
Patent 5999932). Again in 2000 a
patent was filed that included a method is provided for preventing the delivery
of unwanted electronic mail messages to a destination client (US Patent
6112227).
In
conclusion, I would have recommended any of these ideas for iPremier and the IT
manager should have looked further into these patents and would have read the
basics of how to use them and implement the steps into their computer
architecture that could have led to a number one online selling site just like
Amazon. The IT manager needs to
know how to search and design patents to keep their company’s intellectual
property safe. Now that you have
the documents and knowledge to make a patent, go make one!
This research was conducted
for the Management of Information Technology class at Southern Polytechnic State
University. The author thanks Dr.
Rich Halstead-Nussloch for his knowledge of managing information systems and
leadership as a lecturer for Southern Polytechnic State University.
The author also thanks Gil Greenberg, Pramit Patel, Harmeet Bhatia and
Thanh Pham for working as a team to bring their ideas together that helped make
this research possible.
Figure 1 –
United States Patent and Trademark
Office. (2010,
August 26). Retrieved November 12, 2012, from http://patft.uspto.gov/
Figure 2 – USPTO Patent
Full-Text and Image Database. (2010, August 26). Retrieved November 13,
2012, from http://patft.uspto.gov/netahtml/PTO/search-bool.html
Figure 3 –
USPTO
Patent Full-Text and Image Database. (2010, August 26). Retrieved November
13, 2012, from
http://patft.uspto.gov/netacgi/nph-Parser?Sect1=PTO2&Sect2=HITOFF&p=1&u=%2Fnetahtml%2FPTO%2Fsearch-bool.html&r=0&f=S&l=50&TERM1=denial&FIELD1=&co1=AND&TERM2=service&FIELD2=&d=PTXT
Figure 4 –
The successful inventor's
guide: How to develop, protect and sell your invention profitably (pp.
186-187). (1965). NJ: Prentice-Hall.
Figure 5 –
DDoS attack.
(2006). In Creating a winning
e-business (2nd ed., pp.
380-381). Boston, MA: Cengage Learning.
Figure 6 –
Patent it yourself (8th ed.,
pp. Appendix 7-16-2B). (2000). Berkeley, CA: Nolo.

Figure 4
(above) – A patent design application
from the 1960’s
Figure 5 below
– DDoS Attack

Applegate, L. M., Austin, R. D.,
McFarlan, F. W., & Applegate, L. M. (2003). The iPremier Company: Denial of
Service Attack. In Corporate
information strategy and management: Text and cases (pp.
491-499). Boston: McGraw-Hill Irwin.
Battle, C. W. (1997). The
patent guide: A friendly guide to protecting and profiting from patents. New
York: Allworth Press.
Carey, C. W., & Friedman, I. C.
(2011). Steve case. In American
inventors, entrepreneurs, and business visionaries (pp.
72-404). New York, NY: Facts On File. Hitchcock, D., Gima, P., & Elias, S.
(2000). Patent searching made
easy: How to do patent searches on the internet and in the library.
Berkeley, CA: Nolo.
Kessler, K. O., & Carlisle, N. V.
(1965). The successful inventor's
guide: How to develop, protect and sell your invention profitably. Englewood
Cliffs, NJ: Prentice-Hall.
McClure, S., Scambray, J., &
Kurtz, G. (2009). Scanning. In Hacking
exposed 6: Network security secrets & solutions (6th
ed., pp. 649-653). New York: McGraw-Hill.
Piyush, R., Wilson, W. J., Haldar,
P. D., Chandler, J., & Debashis, W. (2012). U.S.
Patent No. 8301712. Washington, DC: U.S. Patent and Trademark Office.
Pressman, D. (2000). Patent
it yourself. Berkeley, CA: Nolo.
Qdata merges with the viascan
group to create canada's leader in barcoding, rfid, and wireless networking
solutions. (2012, February 28). Canada
Newswire. Retrieved November 08, 2012, from
http://ehis.ebscohost.com/eds/detail?sid=af851f54-cc0f-4f83-9361-132073b99879%40sessionmgr111&vid=3&hid=103&bdata=JnNpdGU9ZWRzLWxpdmUmc2NvcGU9c2l0ZQ%3d%3d#db=bwh&AN=201202281452CANADANWCANADAPR.C8155
Robert D. Austin, L. L. (2007,
07 26). iPremier Co. (A): Denial of Service Attack. Harvard
Business
Publishing.
Stim, R. (2009). Patent,
copyright & trademark. Berkeley, CA: Nolo.
Travers, B., & Muhr, J. (1994).
Code and cipher. In World of
invention (pp. 147-521). Detroit,
MI: Gale Research.